CrowdStrike data in detections¶
The CrowdStrike integration blends CrowdStrike EDR with Investigator network detection capabilities and maps Corelight IP addresses from detections to CrowdStrike host information. The expanded data provides additional context to analyze threats and helps analysts make informed decisions during the triage process.
With a CrowdStrike integration configured and enabled, the detections show additional host information from CrowdStrike data to provide even more context. The detection summary highlights some of the most important host information, and the detection details show greatly expanded entity information with even more context.
The CrowdStrike information is seamlessly integrated with the Investigator content. To view the enhanced entity content, go to the Detections page, click a detection, and review the Entity section.
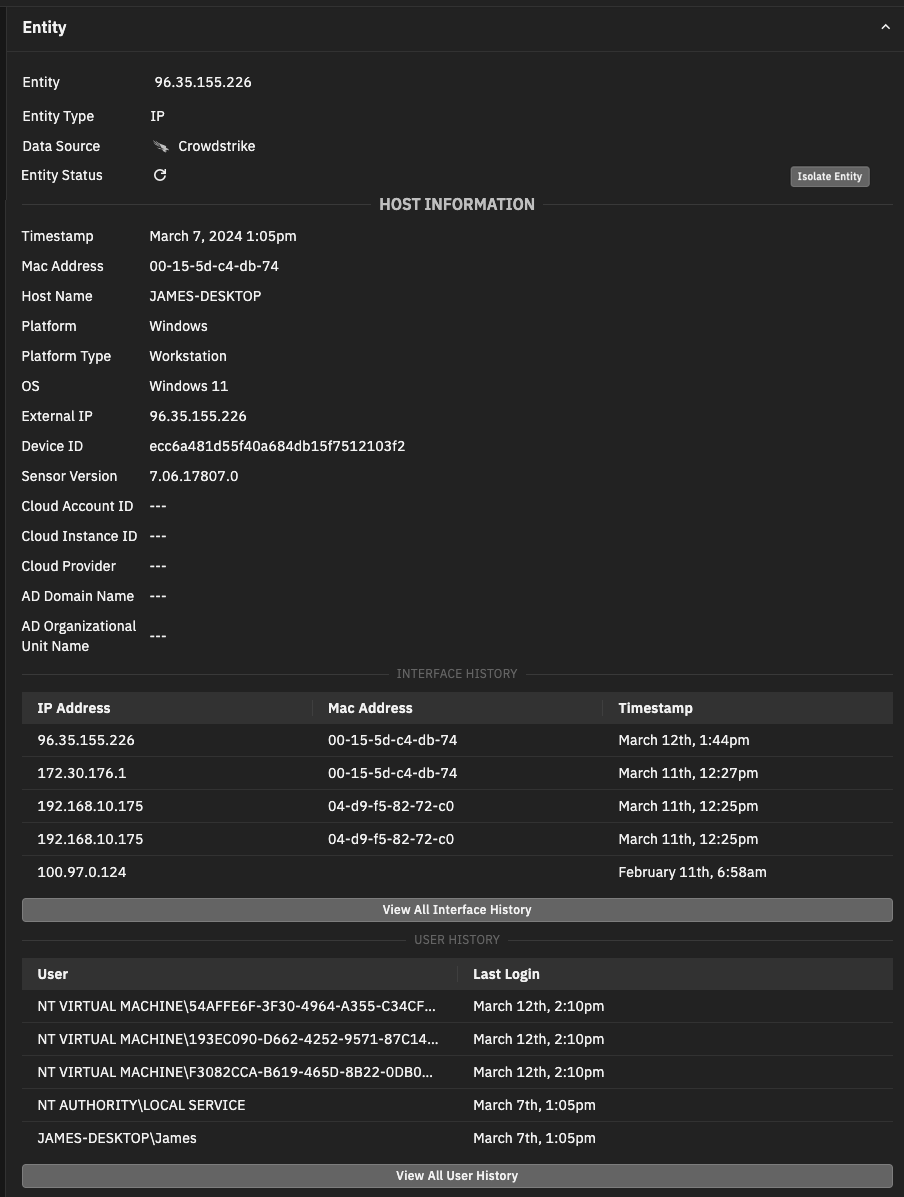
With this integration, you can see the following fields in the associated with entities in the detection details page and the table view of detections.
Field
Description
Timestamp
The timestamp of device’s most recent connection to Falcon.
MAC Address
The MAC address of the device.
Hostname
The name of the machine.
Platform
The operating system platform, such as Linux, Mac, or Windows.
Platform Type
The name of the product type, such as Workstation, Server, or Domain Controller.
OS
The version of the operating system, such as Windows Server 2012 R2.
External IP
The external IP address of the device, as seen by CrowdStrike.
Device ID (Host ID)
The ID of the device, which is obtained from CrowdStrike. You can use this ID to look up information in the CrowdStrike console.
Sensor Version
The version of the CrowdStrike sensor, such as 7.06.16108.0.
Cloud Account ID
The cloud account ID, if applicable.
Cloud Instance ID
Cloud resource information, if applicable.
Cloud Provider
The cloud service provider, such as AWS_EC2_V2, if applicable.
AD Domain Name
Active Directory domain name.
AD Organizational Unit name
Active Directory organizational unit name.
Interface History
The Interface History displays the most recent IP addresses and MAC addresses used by a host and a timestamp indicating the time of access. The 5 most recent entries appear; click View All Interface History to see more entries.
User History
The User History displays the most recent user accounts to log in to the device and the time of their last login. The 5 most recent entries appear; click View All User History to see more entries.
Isolate entities¶
With a CrowdStrike integration configured and set up to isolate entities, admin users can quickly isolate an entity from all network activity to address potential compromises or ongoing attacks based on Corelight evidence. The entity isolation uses the Network Contain feature in CrowdStrike Falcon and CrowdStrike Falcon must recognize the entity.
As an admin user, you can isolate an entity and quickly respond to an attack by implementing quarantine measures. The entity isolation is integrated into the Investigator detection workflow.
The Entity Status field reflects the current state of network containment for the entity.
To isolate an entity
From the Entity section of the Detections detail page, or from the table view of detections, click an entity (IP address or domain).
A dialog box appears that shows available entity details.
You can also mouse over an IP address and choose Investigate | View Details to view the enhanced entity information.
Click Isolate Entity, and when prompted to confirm the action and click Isolate Entity again.
Investigator submits the request to trigger the Network Contain feature in CrowdStrike Falcon and implements quarantine measures for the specified entity.
When submitted, the entity status changes to Pending Isolation and then to Isolated when the request succeeds. (An unsuccessful request displays an error message to help you understand and address the issue.)
When isolated, the entity loses the ability to make network connections to anything other than the CrowdStrike cloud infrastructure. Also, the Isolate Entity buttons changes to a Lift Isolation button.
To remove a device from network isolation
From the Entity section of the Detections detail page, or from the table view of detections, click an entity (IP address or domain).
Click Lift Isolation, and when prompted to confirm the action and click Lift Isolation again.
Investigator submits the request and the entity status changes to Pending Lift and then to Normal, and the device resumes normal network activity.
Note
Analyst users can see the Isolate Entity and Lift Isolation buttons, but cannot perform the related actions.
Additional learning resources¶
Watch a Corelight video on YouTube: CrowdStrike Host Isolation Integration