Security and network overview¶
The Dashboard page appears when you log in. This page provides a high-level summary of what’s going on in your network based on the data coming into Investigator from your sensors. Tabs appear on the top of the page that let you navigate through the dashboards and different views of the data.
By default, the Dashboard page displays the Security dashboard. This dashboard summarizes data about detections on your network, including the number of detections over time and the distribution of detections across MITRE ATT&CK categories as well as information about individual detections.
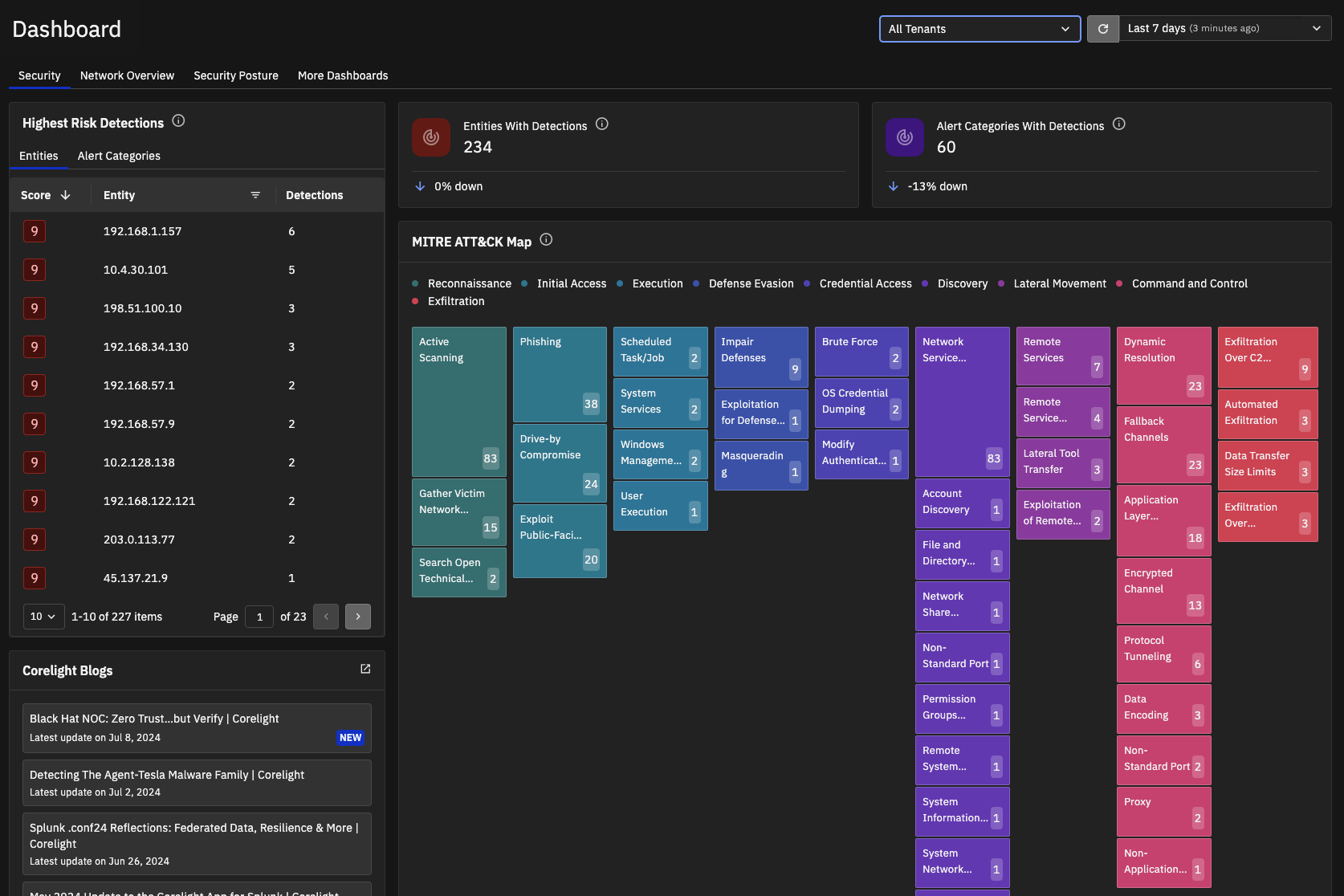
The Security dashboard organizes information in these cards:
Highest Risk Detections - highlights important alerts and alert categories. You can switch between these tabs:
Entities - Displays the entities with the highest severity scores for open detections. The score ranges from 1 to 10 with higher scores indicating more severe threats.
Mouse over an entity to see more information about its associated alert categories and click View Detections to see the detections for the entity in the Detection summary page.
Entities with high threat scores are a good place to start your analysis.
Alert Categories - Displays the alert categories with open detections and their severity score.
Entities with Detections - Displays the number of entities (IP addresses and domain names) flagged with a security alert. The card also shows the percentage change from the previous time window. The number of entities includes both open and closed detections.
Alert Categories with Detections - Displays the number of distinct detection types (both open and closed) identified in the specified time interval. This section also shows the percentage change from the previous time window.
MITRE ATT&CK Map - Provides a heat map that aligns security alerts with MITRE ATT&CK tactics, techniques, and procedures. The MITRE ATT&CK framework shows how attacks evolve through an enterprise.
This card shows the observed tactics (such as reconnaissance and initial access execution) and techniques in the color-coded blocks.
For active scanning alert categories, a number in the bottom-right corner of each card shows how many unique entities were found for the category. Mouse over the color coded technique blocks for details about the associated detections.
For more information about the MITRE ATT&CK framework, see https://attack.mitre.org.
Blogs - Populated with the latest security blogs from Corelight on corelight.com.
You can focus the contents of the page by specifying a time interval from the menu in the upper-right corner. The default time interval is 7 days. You can change the time period to range from one hour to three months, or you can specify a custom date range. The time interval applies to all parts of Investigator and changing the time interval in one place changes it for all features with a time interval. For example, the Detections page uses the same time interval as the Security Overview page.
Tip
You can download the contents of the Security Overview page to a PDF file by clicking the download icon in the bottom-right corner of the page.
The Investigator pages do not automatically refresh. If new detections are available for your time window, the Refresh icon to the left of your time interval selection is blue. Click the Refresh icon to show the new detections in the results. If new detections are not available, the Refresh icon is gray. The time window shows the length of time since the last update.
To learn more about these entities and alerts, go to the Detections dashboard.
You can explore more data through the dashboard tabs under the page title.
Threat Hunting – shows a curated set of hunt queries, organized by category. You can use the vertical ellipse to pivot directly to events.
Network Overview – shows essential network information to answer important questions, including what network technologies are in use, what systems are providing core services/access services/file transfer services, plus bandwidth measurements and conversation tracking.
Security Posture – provides high-level insight into your cybersecurity readiness and the notable events in your environment. This dashboard shows all events from a customizable time range (the default is 24 hours), and lets you filter based on internal/external sources, sensor groups, and sensors.
Some key elements of the Security Posture dashboard are:
SSH Hygiene indicators – a group of dashboard panels offering valuable insights into SSL, x509 and SSH logs to show the health of all certificates, encrypted traffic, and certificate utilization.
DNS Hygiene indicators – A group of dashboard panels with DNS related searches providing insights for NXDOMAIN responses, internal DNS servers, failed DNS queries, unusual query types, and geolocation of common connections.
Remote Activity Hygiene indicators – a group of dashboard panels with insights into top VPN destinations by country, outbound VP connections, and RDP authentication attempts.
Hover the mouse over the Dashboard icon in the left navigation or click the More Dashboards tab to see all available dashboard views, or to create a new dashboard. For more details, see Explore data through Dashboards.