MS Defender data in detections¶
The Microsoft Defender integration blends Defender EDR with Investigator network detection capabilities and maps Corelight IP addresses from detections to Defender host information. The expanded data provides additional context to analyze threats and helps analysts make informed decisions during the triage process.
With a Microsoft Defender integration configured and enabled, the detections show additional host information from Defender data to provide even more context. The detection summary highlights the most important host information, and the detection details show expanded entity information with even more context.
The Defender information is seamlessly integrated with the Investigator content. To view the enhanced entity content, go to the Detections page, click a detection, and review the Entity section.
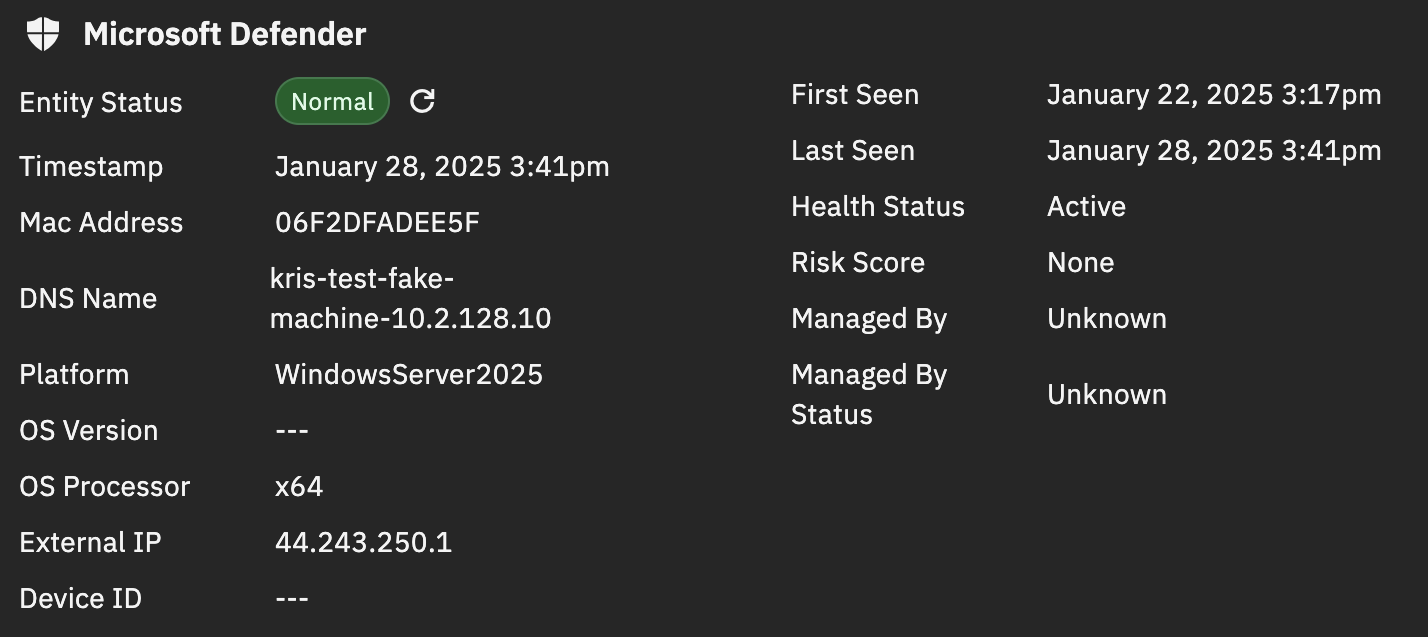
With this integration, you can see the following fields in the associated with entities in the detection details page and the table view of detections.
Field
Description
Timestamp
The timestamp of device’s most recent connection to Defender.
MAC Address
The MAC address of the device.
DNS Name
The device domain or hostname on the network.
Platform
The operating system on the device.
OS Version
The version of the operating system.
OS Processor
The type of processor (CPU) architecture used by the operating system running on the device, such as x64.
External IP
The external IP address of the device, as seen by Defender.
Device ID (Host ID)
A unique identifier assigned to the device within the Defender system.
First Seen
How long ago the device was first seen on the network or when it was first reported by the Microsoft Defender sensor.
Last Seen
How long ago the device was last seen on the network or when it was most recently reported by the Microsoft Defender sensor.
Health Status
The current operational and security health status of the device based on Defender for Endpoints assessments.
Risk Score
A numerical representation of the security risk associated with the device.
Managed By
The entity or system responsible for managing the device’s security and configuration.
Managed By Status
Indicates if the device is actively managed by the specified entity or system.
Isolate entities¶
With a Microsoft Defender integration configured and set up to isolate entities, admin users can isolate an entity from all network activity to address potential compromises or ongoing attacks based on Corelight evidence. The entity isolation uses the isolate devices feature in MS Defender and Defender must recognize the entity.
As an admin user, you can isolate an entity and respond to an attack by implementing quarantine measures. The entity isolation integrates with the Investigator detection workflow.
The Entity Status field reflects the current state of network containment for the entity.
To isolate an entity
From the Entity section of the Detections detail page, or from the table view of detections, click an entity (IP address or domain).
A dialog box appears that shows available entity details.
You can also mouse over an IP address and choose Investigate | View Details to view the enhanced entity information.
Click Isolate Entity, and when prompted to confirm the action and click Isolate Entity again.
Investigator submits the request to implement quarantine measures for the specified entity.
When submitted, the entity status changes to Pending Isolation and then to Isolated when the request succeeds. (An unsuccessful request displays an error message to help you understand and address the issue.)
When isolated, the entity loses the ability to make network connections to anything other than the MS Defender cloud infrastructure. Also, the Isolate Entity buttons changes to a Lift Isolation button.
To remove a device from network isolation
From the Entity section of the Detections detail page, or from the table view of detections, click an entity (IP address or domain).
Click Lift Isolation, and when prompted to confirm the action and click Lift Isolation again.
Investigator submits the request and the entity status changes to Pending Lift and then to Normal, and the device resumes normal network activity.
Note
Analyst users can see the Isolate Entity and Lift Isolation buttons, but cannot perform the related actions.