Palo Alto integration¶
With a Palo Alto integration, you can block IP addresses at the firewall that you have confirmed to be a threat. The integration uses an External Dynamic List (EDL) sourced from an S3 bucket to block specific IP addresses on your Palo Alto firewall. You can update the list through the detection triage process and add or remove threats.
To configure the integration, you need to create an EDL for IP addresses, store it in an S3 bucket with appropriate access, and create an IAM user with a policy defined for access. Next, configure your Palo Alto firewall with the EDL and S3 bucket details. Finally, configure the integration within Investigator.
To create the S3 bucket for the blocklist
In Amazon S3, create a general purpose bucket.
For details, see this AWS help topic: Creating a general purpose bucket.
Edit the bucket policy.
Click the bucket name, click Permissions, and click Edit for the bucket policy.
For details, see this AWS help topic: Adding a bucket policy by using the Amazon S3 console.
Add a policy that defines the S3 location and name of the blocklist file and the IP address for the Palo Alto service.
This policy allows access to the blocklist, but only from the specified IP address. Replace
your-bucket-nameandyour/path/to/blocklist.txtwith your S3 bucket and blocklist path.1{ 2"Version": "2012-10-17", 3"Statement": [ 4 { 5 "Effect": "Allow", 6 "Principal": "*", 7 "Action": ["s3:GetObject"], 8 "Resource": "arn:aws:s3:::your-bucket-name/your/path/to/blocklist.txt", 9 "Condition": { 10 "IpAddress": { 11 "aws:SourceIp": "3.235.101.57/32" 12 } 13 } 14 } 15] 16}
To create an IAM user to allow Investigator to access the S3 bucket
In IAM, go to Access Management | Users and click Create User.
Specify a user name and click Next.
To set permissions, select Attach policies directly and click Create policy.
In the policy editor, click JSON.
Modify and add the following IAM policy to the IAM user. Replace
your-bucket-namewith the name of your S3 bucket, andyour/path/to/blocklist.txtwith the full path to the blocklist file.1{ 2"Version": "2012-10-17", 3"Statement": [ 4 { 5 "Sid": "ListBucketPermission", 6 "Effect": "Allow", 7 "Action": ["s3:ListBucket"], 8 "Resource": [ 9 "arn:aws:s3:::your-bucket-name" 10 ], 11 "Condition": { 12 "StringEquals": { 13 "s3:prefix": [ 14 "your/path/to/blocklist.txt" 15 ] 16 } 17 } 18 }, 19 { 20 "Sid": "PutObjectPermission", 21 "Effect": "Allow", 22 "Action": ["s3:PutObject"], 23 "Resource": [ 24 "arn:aws:s3:::your-bucket-name/your/path/to/blocklist.txt" 25 ] 26 } 27] 28}
Review and create the policy, add the policy to user permissions, and then create the user.
Create an access key and secret key for the IAM user.
For details, see this AWS help topic: How an IAM administrator can manage IAM user access keys.
To configure the EDL in a Palo Alto firewall
Log in to your Palo Alto firewall.
Go to Objects | External Dynamic Lists and click Add.
Enter a descriptive name for the list.
In the Source field, enter the full pathname and filename for the blocklist file in S3.
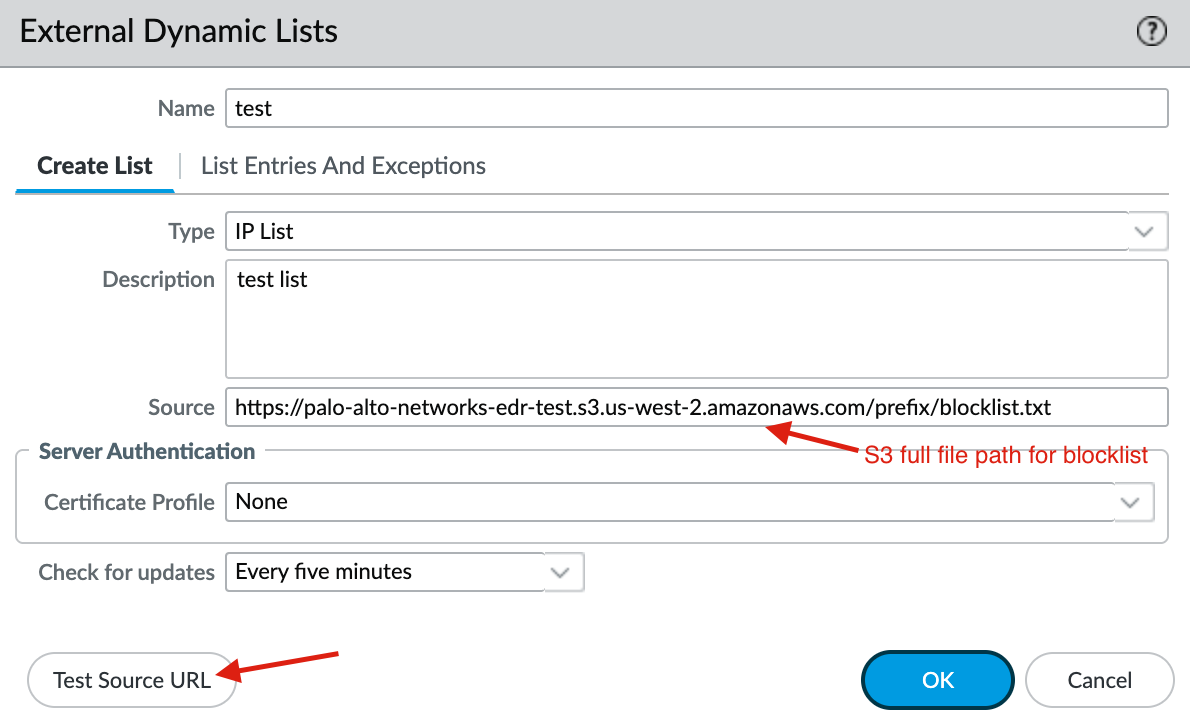
Click Test Source URL to verify the URL is accessible.
Click OK.
Click Commit.
To integrate Palo Alto with Investigator
From System Settings in the left navigation, choose Integrations.
In the Integrations tab, click the Palo Alto card.
Click Configure.
An integration dialog box appears.
Toggle the integration value to Enabled.
Enter your Access Key and Secret Key.
These are the credentials to access your AWS S3 bucket with the EDL file.
Specify the S3 Bucket.
Provide the name of the AWS S3 bucket with the EDL file used by the Palo Alto firewall.
In the S3 File Prefix field, specify the path and name of the EDL, such as
directory/blocked_ips.txt.Specify the S3 Region for the S3 bucket.
For example,
us-east-2.Click Verify Connection to ensure Investigator can use these credentials to update the EDL.
You cannot save your connection until you verify it.
Click Save.
Within Investigator, you need admin access to configure this integration. (Analyst users can view the integration but cannot make changes.)
If you want to pause the integration, toggle the integration setting to Disabled. This preserves your connection details.
If you want to disable the integration and delete your connection details, click the Delete icon.
When configured, you can block and unblock IP addresses for your Palo Alto firewalls.