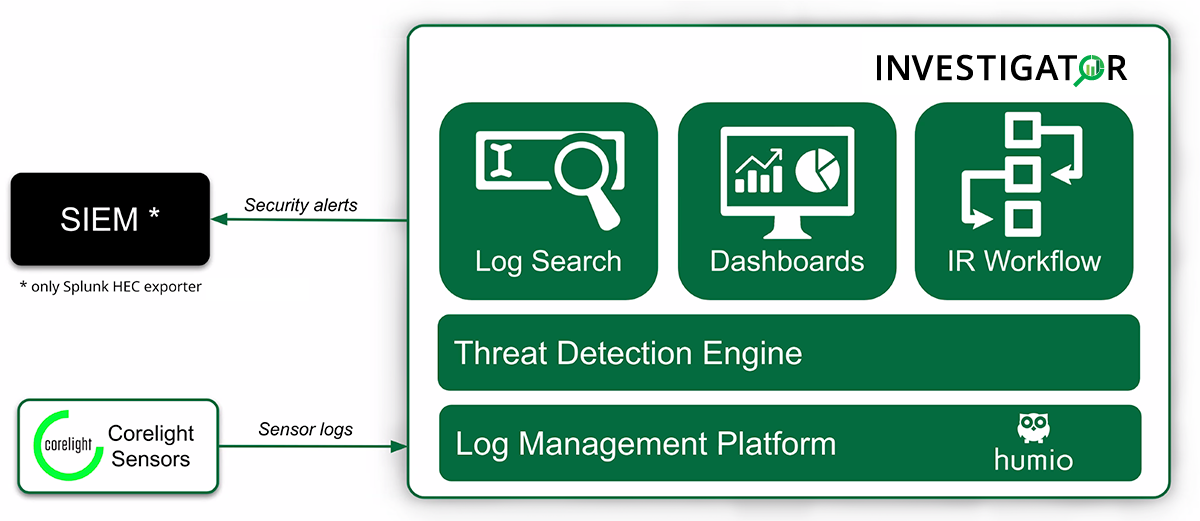
Working with Investigator¶
Corelight Investigator is a cloud-based security platform that provides threat detection and investigation, incident response, and log storage with scalable search. The platform combines Corelight’s rich logging framework with Investigator's sophisticated analytics engine and gives security responders a clear path to identifying and understanding potentially malicious traffic.
Corelight Investigator is a software-as-a-service (SaaS) platform so you don’t need to manage installations, upgrades, or storage systems. Investigator is accessible directly from a browser and receives automatic updates.
Connect one or more Corelight Sensors to Investigator and get immediate access to its powerful analytics engine. See the Quickstart for details.
Watch a Corelight YouTube video with an overview of Investigator.
Alerts¶
As the sensor exports logs, Investigator uses a variety of detection mechanisms to raise specific categories of security alerts.
Notice - Alerts related to notice logs generated by the sensor, Corelight collections, or custom scripts.
Suricata - Alerts resulting from your configured Suricata ruleset on a sensor.
Machine Learning - Alerts raised by the Investigator analytics engine after Corelight logs pass through machine learning models.
Search Based - Alerts generated by Corelight-defined log search queries. The Corelight Labs team creates these alerts using LogScale searches. This alert type provides expanded coverage and rapid response.
YARA - Alerts generated based on your configured YARA ruleset on a sensor.
Anomaly - Alerts resulting from your configured Anomaly Detection use cases on a sensor.
Each alert is associated with an entity – the host domain or IP address – that Investigator identifies as associated with a potential threat. Alerts are assigned a score based on the likelihood that the alert represents a real security threat. The score ranges from 1 to 10, with higher scores indicating more severe threats. Investigator normalizes scores across alert types. You can customize the severity score in the Alert Catalog.
This information lets you identify, prioritize, and respond to security incidents on your network.
There can be anywhere from 10 to 10,000 alerts within a week for an alert category. The volume of alerts can be overwhelming and often analysts are unsure of any required actions. That’s where detections can help.
Detections¶
A detection is an aggregation of alerts from the same alert category and entity combination. The detection can include Suricata, Notices, YARA, search-based, anomaly, and ML alerts or a combination of these alerts.
Through the Detections page, Investigator helps you manage the alert triage process with simplified workflows and instructions to process and resolve the alerts. Investigator leverages Zeek data along with the transparency of machine learning models to provide context and helpful information to take the next steps.
AI-generated content¶
Investigator uses GPT by OpenAI to generate descriptions, next steps, and additional details for some alerts. For example, for Suricata rules, Investigator sends the rule definition to GPT to create a meaningful explanation of the alert and provide recommendations for next steps.
Investigator identifies GPT generated content and features with this icon: ![]()
Note
Content generated through AI might have errors or omissions. Use your best judgment when working with this content.
For more information about AI and the GPT integration, see GPT integration.
Analytics engine¶
The analytics engine is a core component of the Investigator platform. In addition to alerts raised by packages on the sensor, the analytics engine provides a layer of insight for security responders.
The analytics engine steps through four phases:
Normalization
Feature computation
Model scoring
Alert aggregation
During normalization, Investigator processes log data and transforms it for the algorithms.
Investigator uses the normalized data for feature computation. In this step, the analytics engine calculates values for characteristics that it deems important in determining whether the log is associated with an attack.
Next, the analytics engine uses the computed feature values for model scoring. Algorithms use the features to assign a numeric score to each enabled model. A higher score indicates a higher likelihood that the data represents the attack that the model specifies.
Finally, the model scoring output and alerts produced by Corelight Sensors are sent to alert aggregation. In this step, the analytics engine detects which entities represent threats and sends those threats to Investigator's detection dashboard.
Roles¶
Investigator provides three types of user roles: analyst, administrator, and viewer.
The analyst role has access to all the entity and alert data and can follow and identify threats. This is the role for a security analyst and threat hunter.
The admin role includes all the data visibility of the analyst, and can also configure system settings to perform tasks such as manage users, connect sensors, set up integrations, and export alerts.
The viewer role is for individuals who need to view detections and their associated data without making modifications to the system or taking action.
Note
Sensors have their own user roles that are managed separately. You will need an admin role on your sensors to configure them for Investigator exports.