Alert Catalog¶
The Alert Catalog is a list of all alert categories in the system. From the Alert Catalog, you can view details about each alert category, customize severity scores, and define entities to exclude from a category. The Alert Catalog also highlights detection methods for entries. The catalog is available to both analysts and admins.
To access the Alert Catalog
From System Settings in the left navigation, choose Alert Catalog.
The Alert Catalog appears as a tab in the System Settings.
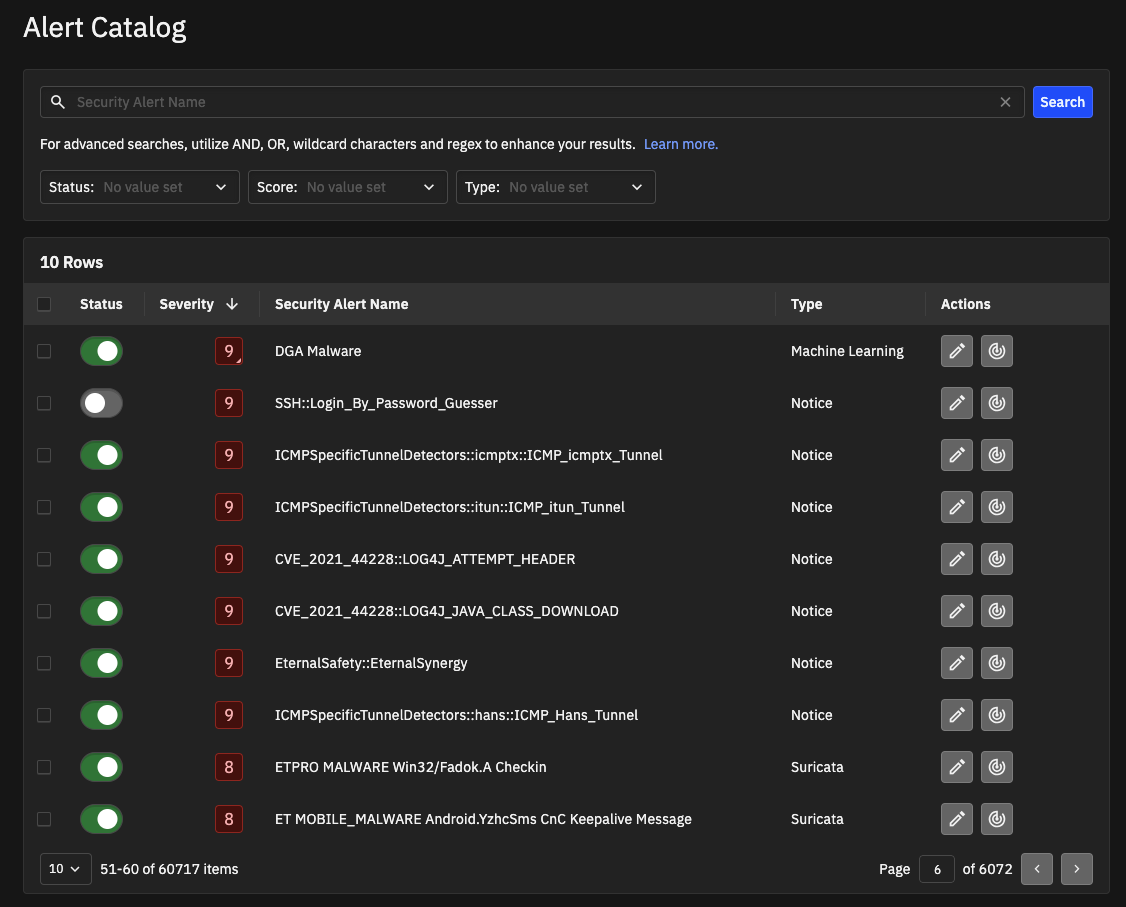
For each alert category in the catalog, you can view:
Status - Active or Inactive. Active alerts are enabled and visible in the dashboard. Inactive alerts are not enabled and are not visible in the dashboard. Click the toggle button to change the status. If an alert is inactive, it is still available in Falcon LogScale (Humio).
You can select multiple alert categories and change their status with a single click.
Severity - A score ranging from 1 to 10 with more severe threats having a higher score. Investigator normalizes scores across alert types.
Security Alert Name - Click an alert category name for the Alert Category details page, which includes:
Info - a description of the alert category (if available)
MITRE ATT&CK mapping to tactics and technique (if available)
Alert properties, including a custom severity score
Excluded entities, which are trusted entities you exclude from the alert category based on IP, domain, or CIDR.
Type - Machine Learning, Notice, Search Based, Suricata, YARA, or Anomaly.
Each alert category includes actions. Actions include:
 Edit Alert opens a dialog box that lets you edit the severity score for the alert.
Edit Alert opens a dialog box that lets you edit the severity score for the alert. View all detections lets you pivot from the category to the Detections page to get more information about all detections associated with the alert category and to take the next troubleshooting steps.
View all detections lets you pivot from the category to the Detections page to get more information about all detections associated with the alert category and to take the next troubleshooting steps.
You can filter alert categories based on these values:
Status - Show only Active or Inactive alerts.
Score - Show only low, medium, or high risk alerts based on their severity score.
Type - Show only machine learning, notice, search based, Suricata, YARA , or anomaly alerts.
You can select multiple filter values from each filter menu.
You can also search for a specific alert category.
Click an entry in the Alert Catalog to view details and properties.
Note
When Investigator identifies a Notice, Suricata, or YARA alert not in the Alert Catalog, Investigator adds the alert to the catalog with an inactive status. You can change the status for this alert to appear in your dashboard. (You can auto-enable YARA alerts.)
Auto-enable YARA alerts¶
As Investigator adds YARA detections to the alert catalog, new YARA rules are disabled by default. You can specify whether these detections should be automatically enabled or remain disabled, requiring manual review and activation. Auto-enablement for YARA alerts simplifies the process by ensuring newly added rules generate detections automatically.
To automatically enable new YARA rules
Click the vertical ellipsis (three stacked dots) in the upper-right corner of the Alert Catalog.
A New Rules Settings dialog box appears.
Select Auto-enable all new rules and click Save.
When you enable this setting, it applies to new rules only and does not affect existing entries in the Alert Catalog.
Update multiple alert categories at the same time¶
You can select multiple alert categories and update their status with a single click. You can select specific entries, all the entries on the page, or all entries across multiple pages. When you select an alert category, a banner appears that provides selection information and options.
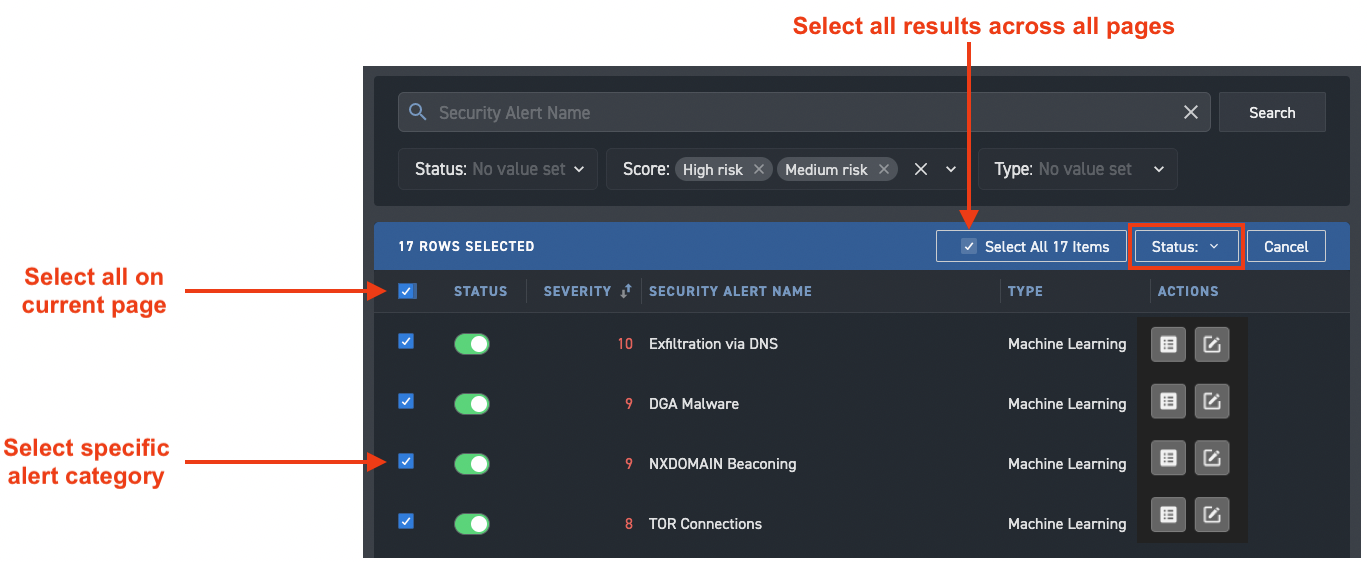
With multiple alert categories selected, use the Status menu to change the status of the selected entries to Active or Inactive.
Tip
Use search and filters to limit the results to make more focused selections.
Exclude entities from an alert category¶
You can exclude entities from an alert category in the Alert Catalog. Excluded entities do not generate new alerts for the alert category. Typically, you exclude trusted entities so you can focus on other entities.
To exclude an entity from an alert category
From the Alert Catalog, click the name of the alert to display the details page.
In the Excluded Entities section, click + Add New.
The right side panel opens.
Choose an Entity Type and enter the corresponding value to identify the entity.
You can exclude Notice and Suricata alerts based on IP address or CIDR. Exclusions for Machine Learning alerts depend on the nature of alert: some Machine Learning alerts let you exclude based on the IP or CIDR and some (such as DNS alerts) let you exclude based on the domain. Similarly, excluding entities from Search Based alerts depends on the nature of alert.
Click Save.
Once saved, specified entities do not generate new alerts for the alert category. Investigator tracks and displays the user who excluded the entity and the time/date the entity was added to the exclusion list.
Click the Delete icon in the Actions column to remove excluded entities.
You can also add an entity to the Excluded Entities list through the Suppress Entity button on the Detections, Entity detail, and Alert detail pages. Similarly, you can use the Unsuppress Entity button to remove an entity from the Excluded Entities list from the Entity detail and Alert detail pages.
Exclude entities from all alert categories¶
Investigator lets admin users globally suppress all alerts for devices identified by an IP address. This helps analysts focus the list of detections by ignoring known, noisy devices (such as security scanners or domain controllers) in the detection queue, and lets analysts focus on more meaningful detections.
To exclude hosts from triggering detections, create a text file with the list of IP addresses to ignore and upload that list to Investigator. When creating the text file, place each IP address to suppress on its own line.
Note
When you suppress alerts and detections for an IP address, the activity for the IP address is still available in the logs and visible in dashboards.
To suppress alerts globally for a device or list of devices
From the Alert Catalog, click Add Global Suppression.
Enter a reason for suppression.
Upload a text (.txt) file that identifies the IP addresses to suppress.
Ensure there is only one IP address per line.
Select the fields for the IP addresses to match.
You can choose Source IP, X-Forwarded-For (XFF), or both.
Click Save.
To make changes to the list of suppressed IP addresses, update the text file. You can simply upload a new version, or download the existing version, make changes, and upload the revised version.
To stop suppressing IP addresses globally, delete the text file with the IP addresses.
If you prefer to suppress an entity for a specific alert category, see Exclude entities from an alert category.
Customize severity scores¶
Investigator lets you change the severity score of an alert category. A custom score overrides the default score assigned by Corelight for alert categories and sets the priority for alert categories. You can revert the custom severity score to the Corelight assigned score. System changes do not override a custom score to an alert category.
By changing the severity score of an alert, you can prioritize the incidents that need immediate attention over those that are less severe. This helps analysts allocate their time and resources more efficiently and address the most critical issues first.
You can also change a security score to reduce false positives and false negatives. An alert might be triggered due to a false positive, which means that the alert is not indicative of a security incident. In such cases, changing the severity score of the alert can downplay the significance of the alert and prevent it from taking up analysts time.
Conversely, there may be situations where an alert is triggered, but the severity score is too low to warrant immediate attention. In such cases, changing the severity score of the alert to a higher value can help to ensure that the incident receives appropriate attention.
Additionally, changing the severity score of an alert can be part of a broader effort to adjust detection thresholds. By changing the threshold values for alerts, analysts can fine-tune the sensitivity of the alerting system to better match the organization’s risk profile and incident response capabilities.
You can update the severity score from the Alert Catalog.
To customize the severity score for an alert category
From the Alert Catalog, click the name of the alert category to display the details page.
Click the Edit Score button under the alert category name.
An Edit Score dialog box appears.
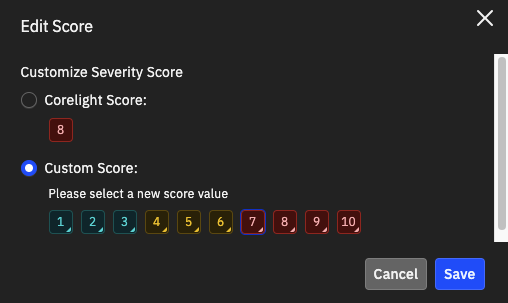
Click Custom Score and click a new score value with 10 indicating the most critical and 1 indicating the least important.
Click Save.
The Properties panel on the alert category details page indicates the custom score for the alert category, and the score icon for an alert category with a custom score changes to include a triangle in the lower-right corner.
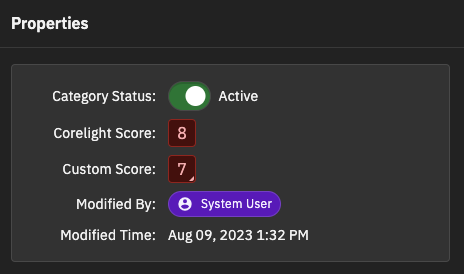
When the custom score is set, all alerts generated in the Alert Category will have the custom score.
Changes to the severity score appear in the Security Audit. The user who modified the alert properties is also identified with the custom severity score.
You can use the Edit Score button to revert to the default Corelight score or adjust the custom score at any time.
Search the Alert Catalog¶
You can search the Alert Catalog based on security alert names. (The search applies to alert titles only and does not include fields and descriptive content.)
The search uses Kibana query language syntax.
Follow these guidelines when creating search queries:
A query can consist of one or more words or a phrase. A phrase is a group of words surrounded by double quotation marks, such as “test search”. Use a phrase to match an exact string.
Combine multiple sub-queries with AND and OR operators. Operators such as AND and OR must be capitalized.
Use parentheses to group sub-queries.
Use wildcards (*) to match multiple values.
Use regular expression (regex) to form complex string queries.
Here are some example search terms:
malware – finds a single phrase
“et dns” – finds the exact phrase in the double quotes
et AND dns – finds results with both terms
et OR dns – finds results with either one of the terms
(ETPRO MALWARE) AND Payloads – finds results with a compound search term and a single search term
nim AND *2 – finds results with the literal phrase (nim) and any other term that ends with a 2
/v1.[0-9]/ – finds results with a literal string (v1.) followed by a number matching a range of numbers from 0 to 9
/mal[a-z]*re/ – finds results with a literal string (mal) followed by a letter matching a range of lower-case letters and then a wildcard in the middle adding flexibility and ending with another literal string (re)
/mal[a-z]*/ – finds a term with a range of letters and a wildcard at the end to allow more options
nim AND /.*2/ – finds the first literal term and the results of the regex construct that finds a term that ends with a 2